How To: Every Mac Is Vulnerable to the Shellshock Bash Exploit: Here's How to Patch OS X
Heartbleed, move over. There's a new bug in town, and this time it's also affecting Mac and Linux computers. It's called Shellshock (its original official title is CVE-2014-6271), and it's currently got a 10 out of 10 severity rating over at the National Cyber Awareness System. While some updates have been issued to fix this bug, they were incomplete, and your system is probably still vulnerable, as it has been for the last probably 20 years.
First Update - 9/26/2014 (Bash Version 3.2.53)A new patch addresses an additional attack vector known as CVE-2014-7169.
Second Update - 9/29/2014 (Bash Version 3.2.53)Apple released an "official" bash update today, and the process is much simpler (just download the .dmg, open the .pkg file, and use their Installer tool) than our manual instructions below because there are no Terminal commands or anything.We've just found out that Apple's patch, while it's listed as bash version 3.2.53, patches the first two initial vulnerabilities and the subsequent ones (see "Third Update" below for info on subsequent exploits).If you're using Yosemite or a system older than Lion, please proceed with our instructions below on manually updating to bash version 3.2.57 using Terminal. Otherwise, Apple's 3.2.53 patch will secure you from most known vulnerabilities; you can download it directly from Apple for:Lion 10.7 (non-English/U.S. versions here) Mountain Lion 10.8 (non-English/U.S. versions here) Mavericks 10.9 (non-English/U.S. versions here) Installing this version will overwrite any changes you made manually when using our guide before—it just replaces the files.Again, if you're on Yosemite, or a version of OS X that's older than Lion, keep reading to see how to manually patch bash for OS X.
Third Update - 10/08/2014 (Bash Version 3.2.57)Several new vulnerabilities have been reported in the weeks following the shellshock discovery. While these are more difficult to exploit as they involve a memory overflow, it would be wise to patch them, too. We've updated our instructions below to include the newest patch.If you followed these instructions before 10:00 a.m. PDT on October 8th, 2014, please delete your bash-fix directory (you can find it in Users -> Username via the Finder) and follow all of the steps below again (starting with Step #1) to ensure that your system is fully patched. If you did not already update manually, then do not delete the bash-fix directory (you probably don't even have one).If you updated using Apple's patch listed above, you do not need to manually update.
What Is Bash?Bash is a command-line shell used in many Linux- and Unix-based operating systems, including Mac OS X. If bash is the default system shell on your computer, it can be used by remote hackers for network-based attacks. With a simple script, a hacker can launch programs or enable features on your computer without any passwords needed and without your knowledge. They could access your files, copy confidential information, delete data, run programs, and more.While the likelihood of your personal Mac being targeted by an attack is relatively small, it's still a big issue that will hopefully get a real and working patch soon. Until then, there are a few things you can do.
Testing for Vulnerability #1In a Terminal window, type in the following command into the shell, followed by the Enter key. Terminal can be found in Utilities in your Applications folders, or via a quick Spotlight search.env x='() { :;}; echo vulnerable' bash -c "echo this is a test"
The Good ResultIf your system is not vulnerable to the Shellshock bug, it will return something similar to the below output.bash: warning: x: ignoring function definition attemptbash: error importing function definition for `x'this is a test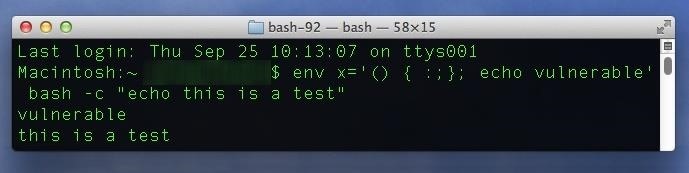
The Bad ResultIf your system is indeed vulnerable to Shellshock, you'll see the following instead.vulnerablethis is a test
Testing for Vulnerability #2 (Added 9/26/2014)If you pass the first test, use the following test to see if you're vulnerable from the second attack vector, which was discovered on Thursday.env X='(){(a)=>\' bash -c "echo date"; cat echo; rm -f echo
The Good ResultIf your system is fine, you'll see something like the following (without any printout of the current date and time).datecat: echo: No such file or directory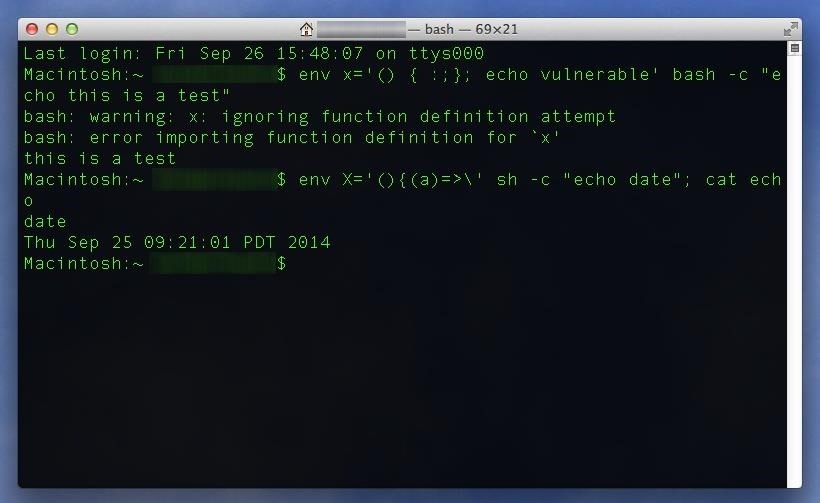
The Bad ResultIf your system is indeed vulnerable to the second attack vector, you'll see the following instead.date<The Current Date and Time>
Testing for Vulnerability #3/4 (Added 9/29/2014)There are no tests yet to check for these new vulnerabilities. Just follow the instructions below to update again and you should be in the clear.
Is There an Update Yet?Many Linux distros have already released patches for Shellshock (though they were mostly incomplete), but Mac OS X has not received anything yet, and Apple hasn't even commented on the issue. There was a recent 10.9.5 update for Mavericks, but it has nothing pertaining to this issue.If you're worried, though, there is a way to manually update your GNU bash version to a more secure one, thanks to some users over at StackExchange.
Check Your Current Bash VersionTo see what version bash you have installed on your Mac, in a Terminal window, enter the following command (followed by the Enter key) into the shell.bash --version If you get GNU bash, version 3.2.51(1)-release, then you'll want to manually update to the newest version of bash 3.2, which is 3.2.57. Also, if you've already used this guide to update to 3.2.52(1)-release or 3.2.53(1)-release, then you'll want to perform everything below again to make sure you're fully protected.There are newer versions of bash out there, but Mac OS X runs off the 3.2 branch. If you're using Linux, you'll want to make sure the patch you download matches the version of bash you're using. The latest patches for all major versions of bash (including 3.0, 3.1, 3.2, 4.0, 4.1, 4.2, and 4.3) can be found here.
Manually Updating Bash - Initial RequirementsYou can manually compile the newest bash version (3.2.57) using the below instructions, but you have to have Apple's Xcode installed on your Mac for this to work. If you don't have it, follow the instructions in the Prerequisite Check section below.If you don't want to update bash, there is a workaround provided by Red Hat, but it hasn't been tested fully, so I wouldn't recommend it.
Prerequisite CheckYou'll need to make sure you have Xcode installed, and have agreed to Apple's terms. For older Macs, you'll also need to make sure you have all the command line tools.You can download Xcode for free from the Mac App Store.If you're on an older version of Mac OS X and Xcode isn't available for you in the Mac App Store, you can download older versions by searching for the proper version number after logging into Apple's developer portal here with your Apple ID. If you're on Mac OS X 10.7 or 10.8, search for "Xcode 4.6.3" in the Downloads for Apple Developers search box on the left side of the page.Once you've installed Xcode, launch it from your Applications folder and agree to Apple's license agreement (the initial launch may take a while). After that, you'll want to confirm that you have all of the command line tools. To do so, do the following:With Xcode open, click the Xcode menu in your top menu bar. Click Preferences. Click the Downloads tab. Click Install next to the Command Line Tools in the list of downloads. Note: If you don't see "Command Line Tools" in the downloads tab, then that means you've already got them and are ready to go!Once done, you have everything you need to patch your system.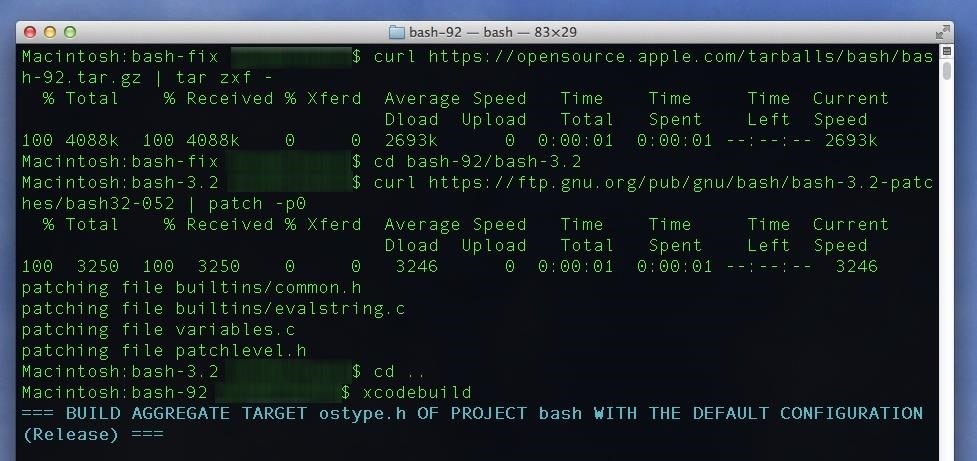
Step 1: Download & Compile the PatchesOnce you've confirmed you have Xcode installed, open Terminal again and enter the following commands. Each bullet point is one command, so make sure you copy the full line in each bullet point (minus the bullet, of course).mkdir bash-fix cd bash-fix curl https://opensource.apple.com/tarballs/bash/bash-92.tar.gz | tar zxf - cd bash-92/bash-3.2 for i in $(seq -f "%03g" 52 57);do curl https://ftp.gnu.org/pub/gnu/bash/bash-3.2-patches/bash32-$i | patch -p0; done cd .. xcodebuild This process may take a while, and you'll see a lot of text appearing in the Terminal window. It's just Xcode compiling the new version of bash on your system. Once it's done, it'll say "BUILD SUCCEEDED" and you'll see a Terminal prompt again.
Step 2: Back Up Your Current Version (Just in Case)Just in case something goes wrong, it's a good idea to back up your current version of bash. That said, if you already did this step in a previous attempt to patch your system, you can skip it as you already have a backup. You can do so by entering the following two commands in Terminal.Note that you'll likely be prompted for a password when doing this step. If so, use the same password you use to log in to your Mac. You will not see your password in Terminal as you type, so it may take you few attempts if you have a complicated password.sudo cp /bin/bash /bin/bash.old sudo cp /bin/sh /bin/sh.old You won't see any confirmation, but it'll work, and if something goes wrong after Step #5 below, you can get back your old un-patched version of bash by reversing the above copy commands, to copy the ".old" copies back over their original files (without the ".old" part).
Step 3: Verify the Version of Your New BuildEnter the following commands in Terminal to verify you've got the new version of the bash build on your computer.build/Release/bash --version build/Release/sh --version The output of these commands should confirm for you that the build version of bash is 3.2.57(1)-release.
Step 4: Replace Your Old Bash with the Patched VersionAlmost done. You just have to copy the new version of bash over your old version. Do so with the following Terminal commands.sudo cp build/Release/bash /bin sudo cp build/Release/sh /bin If you want to verify that you have the newest version as your default bash, just run the check bash version command again.bash --version And that's it. Now just try out the test again and if it comes back with the good result (i.e., not the one that says "vulnerable"), then you're golden.env x='() { :;}; echo vulnerable' bash -c "echo this is a test" And run the second test to confirm the current date and time don't print out:env X='(){(a)=>\' bash -c "echo date"; cat echo; rm -f echo If the date does print out again, first check your user home directory to see if a file called "echo" was created when you ran the test the first time. If so, delete it and run the test again. If the date still prints out, chances are you missed part of the updated Step #1 above. If you ever think you might of messed up a command, you can always start over by deleting your bash-fix folder and starting again from Step #1. Also note that you can delete the bash-fix folder if you're all good, too, because it's just a temporary folder.
For Homebrew or Macports UsersIf you use Homebrew or Macports, you can get instructions on updating bash over at StackExchange.
The instructions now fully address both vulnerabilities and should be the last patch you need to perform. What Is Bash? Bash is a command-line shell used in many Linux- and Unix-based operating systems, including Mac OS X. If bash is the default system shell on your computer, it can be used by remote hackers for network-based attacks.
Every Mac Is Vulnerable to the Shellshock Bash Exploit: Here
Every Mac Is Vulnerable to the Shellshock Bash Exploit: Here
The vulnerability is called Shellshock, and it has rocked the security industry to its core. A flaw in the "Bash" shell—the command line interpreter for Unix-based systems including Linux and Mac OS X—has sent server administrators scrambling to patch their systems. Security experts are
Bash shell 'Shellshock' flaw opens OS X, Linux, more to
With the announcement of the Shellshock Bash Bug, Linux admins around the world have been scrambling to patch their Bash shells so that they're no longer vulnerable to the exploit. If you have a Fedora, RHEL, or CentOS system that hasn't reached End-Of-Life, then updating to a patched version of Bash is as simple as: sudo yum update -y bash
Shellshock Bash Bug - Byteworks
'Bigger than Heartbleed' Shellshock flaw leaves OS X, Linux, more open to attack Graham and Ars Technica report that Mac OS X Mavericks contains a vulnerable and Apple will no doubt patch
Every Mac Is Vulnerable to the Shellshock Bash Exploit: Here's How to Patch OS X. First, the "legal" stuff. If you decided to follow these steps, and something breaks - ITPro-Blog.com can in no way be held liable.
Shellshock Bash Exploit: Patch OS X - A Geek to Go, LLC
It is likely that all un-patched versions of Linux and Unix, including OS X, are affected by this vulnerability. Details of actual exploits are still emerging, but reports indicate that SSH and web servers with CGI components are likely vectors for perpetrating an attack.
Shellshock Vulnerability: What Mac OS X Users Need to Know
Due to the sheer amount of -nix systems, including Apple's OSX Operating System, that utilize some version of the Bash shell, this vulnerability is highly-regarded as one of the biggest security vulnerabilities in history. What exactly is a "Bash"?
Security Update: Bash "Shellshock" Vulnerability - Jamf
The instructions now fully address both vulnerabilities and should be the last patch you need to perform. What Is Bash? Bash is a command-line shell used in many Linux- and Unix-based operating systems, including Mac OS X. If bash is the default system shell on your computer, it can be used by remote hackers for network-based attacks.
Every Mac Is Vulnerable to the Shellshock Bash Exploit
Again, if you're on Yosemite, or a version of OS X that's older than Lion, keep reading to see how to manually patch bash for OS X. Third Update - 10/08/2014 (Bash Version 3.2.57) Several new vulnerabilities have been reported in the weeks following the shellshock discovery.
Every Mac Is Vulnerable to the Shellshock Bash Exploit: Here
Home » Every Mac Is Vulnerable to the Shellshock Bash Exploit: Here's How to Patch OS X Heartbleed, move over. There's a new bug in town, and this time it's also affecting Mac and Linux computers.
How to Manually Update Bash to Patch Shellshock Bug on Older
0 comments:
Post a Comment